WHAT :K8S API的标准资源类型之一,也是核心资源,它是基于域名和URL路径,把用户的请求转发至指定Service资源的规则
- 将集群外部的请求流量,转发至集群内部,从而实现“服务暴露”
- nginx + go脚本
WHY :上面实现了服务在集群“内”被自动发现,那么需要使得服务在集群“外”被使用和访问,常规的两种方法:
- 使用NodePort型的service
- 无法使用kube-proxy的ipvs模型,只能使用iptables模型
- 使用ingress资源
- 只能调度并暴露7蹭应用,特指http和https协议
以trafiker为例
WHAT :为了让部署微服务更加便捷而诞生的现代HTTP反向代理、负载均衡工具。
WHY :可以监听你的服务发现/基础架构组件的管理API,并且每当你的微服务被添加、移除、杀死或更新都会被感知,并且可以自动生成它们的配置文件
# 200机器,部署traefiker(ingress控制器)
cd /data/k8s-yaml/
k8s-yaml]# mkdir traefik
k8s-yaml]# cd traefik/
traefik]# docker pull traefik:v1.7.2-alpine
traefik]# docker images|grep traefik
traefik]# docker tag add5fac61ae5 harbor.od.com/public/traefik:v1.7.2
traefik]# docker push harbor.od.com/public/traefik:v1.7.2
复习:mkdir 创建目录、cd 移动到其它目录、
docker pull 下载镜像、docker tag 打标签、docker push 上传到仓库
# 200机器,准备资源配置清单(4个yaml):
traefik]# vi rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRole
metadata:
name: traefik-ingress-controller
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses
verbs:
- get
- list
- watch
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-ingress-controller
subjects:
- kind: ServiceAccount
name: traefik-ingress-controller
namespace: kube-system
traefik]# vi ds.yaml
apiVersion: extensions/v1beta1
kind: DaemonSet
metadata:
name: traefik-ingress
namespace: kube-system
labels:
k8s-app: traefik-ingress
spec:
template:
metadata:
labels:
k8s-app: traefik-ingress
name: traefik-ingress
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 60
containers:
- image: harbor.od.com/public/traefik:v1.7.2
name: traefik-ingress
ports:
- name: controller
containerPort: 80
hostPort: 81
- name: admin-web
containerPort: 8080
securityContext:
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
args:
- --api
- --kubernetes
- --logLevel=INFO
- --insecureskipverify=true
- --kubernetes.endpoint=https://10.4.7.10:7443
- --accesslog
- --accesslog.filepath=/var/log/traefik_access.log
- --traefiklog
- --traefiklog.filepath=/var/log/traefik.log
- --metrics.prometheus
traefik]# vi svc.yaml
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress
ports:
- protocol: TCP
port: 80
name: controller
- protocol: TCP
port: 8080
name: admin-web
traefik]# vi ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: traefik-web-ui
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: traefik.od.com
http:
paths:
- path: /
backend:
serviceName: traefik-ingress-service
servicePort: 8080
每次有ingress时,我们第一反应就是要去解析域名
这里为什么我们都可以把什么都丢到80端口,是因为现在已经是Pod了,已经隔离了,无所谓你用什么端口
# 21/22任意机器(我用的22),应用资源配置清单:
~]# kubectl apply -f http://k8s-yaml.od.com/traefik/rbac.yaml
~]# kubectl apply -f http://k8s-yaml.od.com/traefik/ds.yaml
~]# kubectl apply -f http://k8s-yaml.od.com/traefik/svc.yaml
~]# kubectl apply -f http://k8s-yaml.od.com/traefik/ingress.yaml
# 下面重启docker服务要在21/22节点都执行,否则会有一个起不来
~]# systemctl restart docker.service
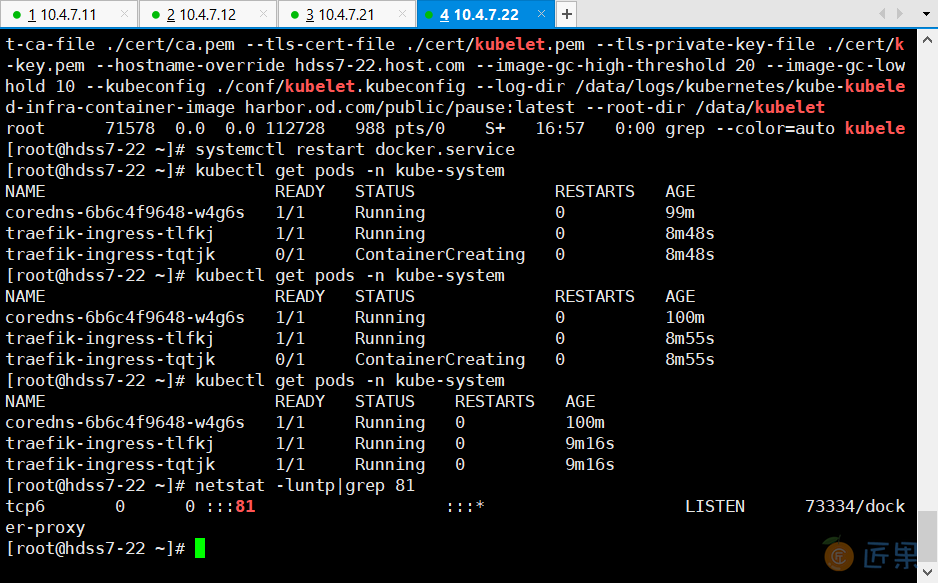
~]# kubectl get pods -n kube-system
~]# netstat -luntp|grep 81
# 11/12机器,做反代:
~]# vi /etc/nginx/conf.d/od.com.conf
upstream default_backend_traefik {
server 10.4.7.21:81 max_fails=3 fail_timeout=10s;
server 10.4.7.22:81 max_fails=3 fail_timeout=10s;
}
server {
server_name *.od.com;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
~]# nginx -t
~]# nginx -s reload
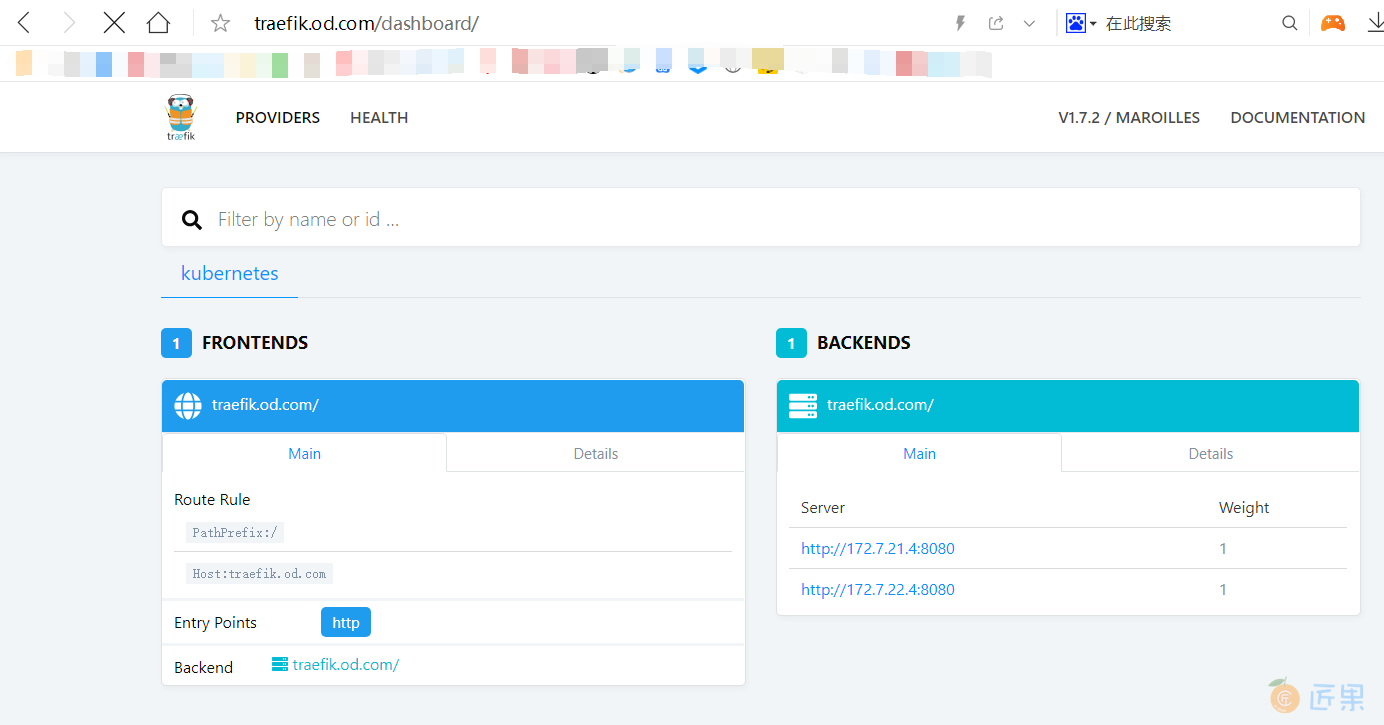
# 11机器,解析域名:
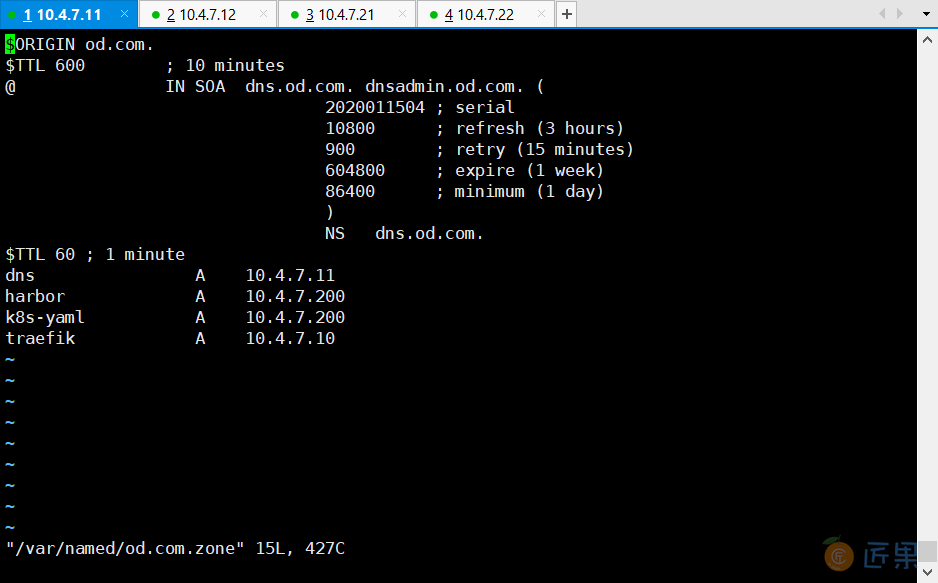
~]# vi /var/named/od.com.zone
前滚serial
traefik A 10.4.7.10
~]# systemctl restart named
nginx -t :检查nginx.conf文件有没有语法错误
nginx -s reload :不需要重启nginx的热配置
用户访问流程:
当用户输入traefik.od.com时,被dns解析到10.4.7.10,而10则在11上,去找L7层服务,而反代配置的od.com.conf,则是将*.od.com无差别的抛给了ingress,ingress则通过noteselect找到pod
再回顾上面的架构图,我们已经全部安装部署完。
接下来,我们就要开始安装部署K8S的周边生态,使其成为一个真正的PaaS服务。 kubernetes 技能图谱
下一节:WHAT:向企业展示度量信息和关键业务指标(KPI)现状的数据虚拟化工具
WHY:我们目前都是用机器去安装部署资源,但我们以后不可能动不动就上主机,那样非常不安全,而且开发人员等也需要看到POD的情况,不可能让他们也登录主机去查看,所以我们需要一个有权限控制的界面展示和控制的工具